Ransomware continues as one of the most prominent cyber security threats in the modern IT security landscape. For the uninitiated, Ransomware is a specific type of malware attack infiltrating your network and encrypting your data. Furthermore, the encryption shuts down your entire network allowing hackers to ransom off an encryption key to decrypt your encrypted data. Ransomware attacks have skyrocketed in popularity recently. The rise correlates to the high-profile nature of several attacks, such as the Colonial Pipeline attack, as well as containing built-in revenue mechanisms allowing hackers to easily profit. In summary, this article discusses the main causes of ransomware attacks and best practices for you to protect your organization.
Main Causes of Ransomware Attacks
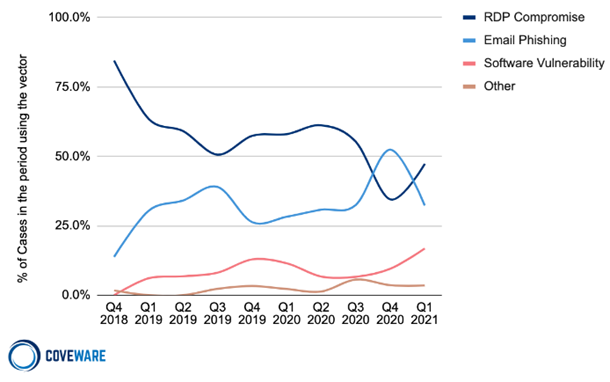
There are two main initial attack vectors for ransomware: Remote Desktop Protocol (RDP) compromise and email phishing. According to a 2020 Incidence Response and Data Breach Report by Palo Alto 50% of ransomware attacks in 2020 had an initial attack vector of RDP compromise, with 43% of attacks carried out through email phishing.
RDP Compromise
Remote Desktop Protocol (RDP) is a protocol built into Microsoft Windows allowing a computer to be controlled remotely by another user. It is a helpful protocol especially for IT service and remote work, but an unsecured RDP is a huge vulnerability that hackers will target. Due to the pandemic, many machines were rapidly partitioned for remote work. If done incorrectly, these machines could become an open door for ransomware. To learn more about RDP check out our blog titled “Remoted Desktop Protocol and The Ransomware Problem“.
Email Phishing
Phishing remains a primary IT security threat. With the proliferation of ransomware, it continues to grow into an even more dangerous attack vector. Over time, hackers have developed more elaborate methods of social engineering, making phishing emails much harder to detect. No matter how secure your IT network is, people will have to interact with it, making humans the obvious weak link in any IT security plan. Additionally, hackers continue to exploit the “human element” and significantly increase the effectiveness of email phishing. For a more detailed look into the threat of email phishing check out our blog titled “Best Ways To Protect Against Email Phishing“.
Protection Tips
Unfortunately, there is not a single solution that 100% ensures protection from ransomware. However, many protocols and software solutions exist designed to lower your chances of being attacked, as well as to mitigate the impact of successful breaches.
To secure your network, here are recommended steps your organization should take:
- Secure your RDP behind a Virtual Private Network (VPN)
- Enable Multi-Factor Authentication (MFA). This means regardless of compromised RDP credentials, a separate layer of security prevents attackers from breaching your network
- Limit Login Attempts. This prevents brute force attacks
- Automatically disconnect RDP sessions that reach a certain time limit of inactivity
- Deploy an Attack Surface Monitoring Solution that monitors your entire network for vulnerabilities
- Provide staff training focused on common email phishing methods
- Implement email security protocols, including the quarantine of suspicious emails
- Implement a robust backup and recovery system
- Encrypt your own data, as well as its backups to protect from Doxware
The most important step in ransomware protection is having a backup and recovery system possessing frequent backups, and quick restorations. If a ransomware attack is successful and you do not have a robust system like this, you will either have to pay a costly ransom or suffer even greater financial losses due to prolonged recovery time. Furthermore, these systems have utility outside of the ransomware space and are crucial to modern IT infrastructure plans. For more information about the growing threat of ransomware, as well as ransomware security solutions use the button below to talk to a cyber security expert at Strategic Communications.
Share this Post

